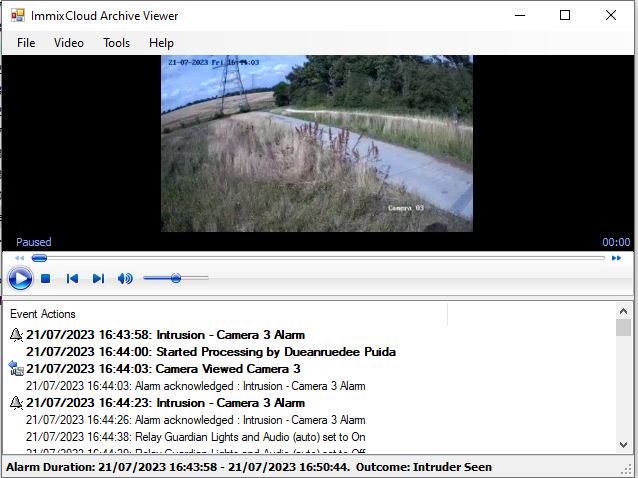
Data and Network Security
Remote Surveillance take data security very seriously, following industry and sector best practice whilst also working with our clients to work within their own environments as needed.
Data Transmission
We will work with you to decide on how your data should move from the camera networks through to our control room, with options ranging from simple firewall based port and IP rules through to point to point connectivity between our firewall and yours using your own VPN.
We run our own VPN based on the OpenVPN protocol which is supported by most of the camera systems and mobile routers we interact with.
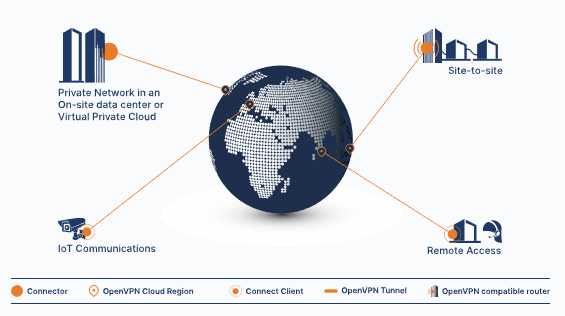
You can find more information here
Business VPN For Secure Networking | OpenVPN
This VPN solution offers many levels of granularity and also gives our control room and IT staff a wealth of dashboard data to help manage the live connectivity.
When used with a compatible router this VPN infrastructure can also dramatically reduce your comms costs as it breaks the reliance on a static IP, allowing for much cheaper 4/5G tariffs to be used.
Data Processing and Storage
Our datacentre is protected by multi-layered physical security and all access into and out of the building is monitored by a visual human check and proximity access tags. Additionally all areas of the datacentre both inside and out are monitored by video surveillance monitored 24/7/365 and digitally recorded
Our datacentre provider is UK Servers who have been providing high availability, mission critical dedicated servers within the UK and Europe since 2004
Your can learn more about the data centre here
Data Access
Your data is usually only ever accessible by your authorised users and our control room staff.
Control room and system access is controlled by username/password and by IP address restrictions, with all activity recorded in the system audit trails.
We will work with you to define an authorised user policy that helps you adhere to your own market, sector of business requirements, ranging from simple username/password through to using your own VPN and port restrictions.
Data Sharing with 3rd Parties
There may be times where you – or us – receive a subject access request. In this situation we can provide a extraction covering the subject access request which can be supplied to the requesting party allowing them to view the material without needing to access our systems or networks.